Everything You Need to Know about Dollar-Denominated Cryptocurrencies

Everything You Need to Know about Dollar-Denominated Cryptocurrencies
A well-known obstacle to the greater popularity of Bitcoin as a medium of payment is the
high volatility of its exchange value. This volatility results from its built-in quantity commitment: because the number of Bitcoins in existence stays on a programmed path, variations in the real demand to hold Bitcoin must be accommodated entirely by
variations in its unit value. When demand goes up, there is no quantity increase to dampen the rise in price; and vice-versa for a fall in demand.
Not surprisingly, several cryptocurrency developers have thought of creating a cryptocurrency with a price commitment–namely a pegged exchange rate with the US dollar–rather than a quantity commitment, in hopes of greater popularity. The aim is to create a system in which dollar-denominated payments can be made with the ease, security, and low cost of Bitcoin payments, but without the exchange-rate risk.
New Digital Assets

The development of “Blockchain 2.0” platforms has enabled the launching of a variety of new digital assets, including such dollar-pegged (and euro-pegged and
gold-pegged) currencies. As we will see, the histories of early (2014-2016) dollar-pegged cryptocurrencies show a series of flops. But one project, Tether, has become a late-blooming success.
Tether had $55 million in circulation as of March 29, 2017, making it the #13 largest cryptocurrency. To keep this size in perspective, a brick-and-mortar US institution with $55 million in deposits is a tiny bank or a mid-size credit union, and Tether is currently only 1/300th the size of Bitcoin.
The
Tether white paper explains in more detail the motivation for developing a dollar-pegged cryptocurrency by listing advantages to individuals using it for dollar-denominated transactions rather than using dollars held in “legacy bank” accounts:
- Transact in USD/fiat value, pseudonymously, without any middlemen/intermediaries
- Cold store USD/fiat value by securing one’s own private keys
- Avoid the risk of storing fiat on [cryptocurrency] exchanges–move cryptofiat in and out of exchanges easily
- Avoid having to open a fiat bank account to store fiat value
In sum, “Anything one can do with Bitcoin as an individual one can also do with” a dollar-pegged cryptocurrency, namely, “avoid credit card [or debit card] fees,” maintain greater privacy, “remit payments globally” more cheaply, and access blockchain financial services.
But what is the claimed advantage over using Bitcoin? It is the expectation of wider acceptance in payments, because of the advantages to merchants of accepting a dollar-pegged cryptocurrency over accepting Bitcoin in a US-dollar-dominated economy:
- Price goods in USD/fiat value rather than Bitcoin (no moving conversion rates/purchase windows)
- Avoid conversion from Bitcoin to USD/fiat and associated fees and processes
The Flops
First we consider the projects that have flopped. Three projects were launched in
September 2014: CoinoUSD, NuBits, and BitUSD. Their pegging mechanisms were different, and are difficult to describe briefly (partly because they were not all entirely transparent), but two common features are important to note.
- The rate-pegging mechanisms were not programmed into a source code, like Bitcoin’s quantity commitment, but relied on non-programmed policy actions by a trusted central authority.
- None used the traditional currency pegging method of having the issuer hold reserves in physical dollars or dollar-denominated debt securities. (On the NuBits mechanism see this critique by a BitUSD promoter. On the BitUSD mechanism see this critique by the CoinoUSD developer.)
We can examine the fortunes of each project by looking at its price and “market capitalization” (value-in-circulation) history on the cryptocurrency tracking site
CoinMarketCap.com.
CoinoUSD
CoinoUSD, which began trading in December 2014, was developed by a for-profit payments firm called Coinomat and built on the blockchain of the NXT cryptocurrency. (In November 2014 NXT was the #6 cryptocurrency with a market cap of $19 million; currently it ranks #38 with a market cap around $13 million.)
CoinoUSD reached a market cap plateau of $2.7 million in early 2016, but shut down in early 2016, due to a “
payout glitch” that flooded customers with free CoinoUSD units, making it impossible to maintain the exchange value at $1. Coinomat
announced a reboot in which the erroneous payout would be reversed and said, “NXTUSD will replace CoinoUSD completely, and enhance it,” but this appears not to have happened. Since then it has had a market cap of zero, and its
webpage at the Coinomat site declares it “disabled until further notice.”
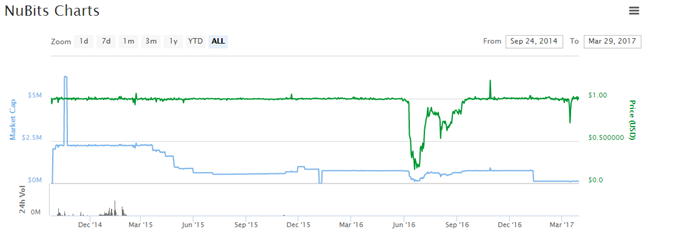
 NuBits
NuBits
The history of NuBits, also a for-profit enterprise, shows that it gained only a similarly small market foothold. Its market cap plateaued early on below $2.5 million, and since April 2015 has remained below $1 million. In June 2016 NuBits had a devaluation crisis, with the price falling to 20 cents. Its
rate-pegging intervention mechanism, despite claiming many layers of reinforcement, was not robust and failed.
Although the price later returned to par, today NuBits shows very little market activity. Since January 2017 the market cap has hovered around only $135,000, with daily trading volume in the neighborhood of $2,000.
 BitUSD
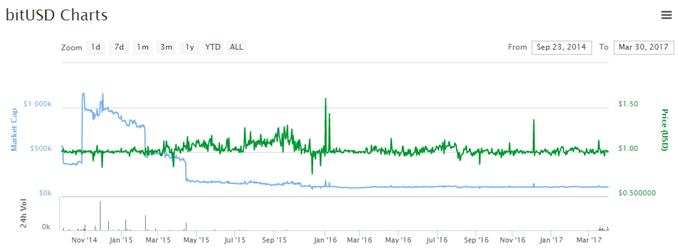
BitUSD
BitUSD is built on the blockchain platform of the cryptocurrency BitSharesX. Its highest market cap plateau was around $1 million soon after introduction, but it fell to below $200,000 in April 2015 and is currently less than $110,000.
BitUSD uses a novel pegging system that so far has proven robust. A piece
promoting BitUSD emphasizes that “the bitUSD is an asset that is not backed by real dollars in someone’s bank account.” (It claims this a virtue: “We cannot trust anyone to hold and secure a physical asset so that people can redeem it eventually. History has repeatedly shown: It doesn’t work!” In fact, history shows the major banks in unhampered banking systems routinely justifying the public’s trust by redeeming their liabilities on demand for decades. Paypal works on the same supposedly non-working model, backed by Paypal’s dollar deposits at Wells Fargo Bank.)
By contrast, BitUSD are created through collateralized forward currency contracts. The network provides an escrow service that credibly ensures repurchase (or “redemption”) of the BitUSD at or near par. Someone who wants to acquire BitUSD, say in order to buy from a seller who prefers a dollar-denominated medium of exchange, offers a contract: so many BitShares (hereafter BTS) for a certain amount of new BitUSD.
Under the BitShare network rules, the acquirer must not only pay at the outset in BTS but also agree to post
collateral in BTS equal to the value of the bid. If the bid is accepted by another network participant, explains the BitUSD
white paper, “the collateral and purchase price are held by the network until the BitUSD is redeemed” by some third party repurchasing it. The acquirer of BitUSD thus puts 200% collateral into a contract “that only allows access to these BTS when the BitUSD are paid back.” In effect the acquirer is shorting the dollar price of BTS.
Note that the new BitUSD units are initially 200% collateralized not in dollar-denominated assets, but in BTS. If BTS fall 25% or more against the dollar, such that the value of the BTS collateral declines to 150% or less of the value to be repaid, under the network rules redemption can be compelled by any BitShares miner who “enforces a margin call.” (It should be noted that to enforce the collateral rules, the BitShares network relies on trusted human agents to inform it about the current $ price of BTS.)
The system then “uses the backing BitShares to repurchase the BitUSD…thereby redeeming it.” Conversion back into dollars is thus not always at the initiative of the holder, as it is for a holder of ordinary demandable bank liabilities. Instead, a BitUSD holder faces a risk of “forced settlement.” If the value of BTS falls so quickly “that the margin is insufficient, then the market price of the BitUSD may fall slightly below parity for a short time if there is insufficient demand for BitUSD relative to the supply of sellers.”
The white paper concludes: “The critical thing to understand is that BitUSD is an asset used to hedge a position in BitShares against changes in the price of USD and is not supposed to have an exact 1:1 exchange rate with USD.” A close look at the chart indeed shows that the price of 1BitUSD has not been exactly $1. It has vibrated around $1 but has not experienced any lasting devaluation. Nonetheless, its clientele has declined and is currently small. No doubt this reflects in part the declining popularity of BTS, its market cap having fallen from more than $60 million in September 2014 to around $15 million today.
The Success: Tether
Now to the success story. Tether was launched in February 2015. In contrast to the previous contenders, as the chart shows, it started slowly and has grown in market cap. The series of discrete steps in its market cap path indicates that there have been a series of large purchases.
The most recent step, on Wednesday, March 29, 2017, raised the value in circulation to $55 million from $45 million. Logically these are not speculative position-takings because there are no capital gains to be had so long as the price per tether remains solidly pegged (or “tethered”) to $1. And Tether has in fact successfully maintained a steady peg throughout its history with only one small and brief blip. The steps are presumably big acquisitions for transaction use. Transactions volume in recent weeks has been running mostly in the neighborhood of at $20-40 million per day.

Tether transfers are executed using the Bitcoin blockchain. Tether’s pegging mechanism is also not programmed into a source code, but it is the traditional one: the issuer holds dollar-denominated reserve assets and pledges to redeem Tethers on demand. (Euro-Tethers have recently been introduced, but I focus here on dollar-Tethers.)
According to the
official FAQ, “Tether Platform currencies are 100% backed by actual fiat currency assets in our reserve account. Tethers are redeemable and exchangeable pursuant to Tether Limited’s terms of service. The conversion rate is 1 tether USD₮ equals 1 USD.”
The parent Tether firm, in other words, operates like a currency board: It holds 100%+ dollar-asset backing, and passively swaps Tethers for dollars and back again. Like a currency board, it can earn interest income by holding some of its dollar-denominated assets in interest-bearing form.
The
Tether white paper reveals that Tether’s dollar reserves are currently held in accounts at two major Taiwanese commercial banks: Cathay United Bank and Hwatai Bank. (Why these particular banks? “They also provide banking services to some of the largest Bitcoin exchanges globally,” they are okay with Tether’s business model, and they are experienced at compliance with Know-Your-Customer and Anti-Money-Laundering regulations.)
It adds that “additional banking partners are being established in other jurisdictions” to reduce political risk of the accounts being frozen. Tether is thus not a “100% reserve” institution in the sense of a money warehouse holding 100% literal cash reserves (which would mean Federal Reserve notes in a vault).
How does a potential purchaser of Tether verify the 100% backing claim? The website declares: “Our reserve holdings are published daily and subject to frequent professional audits. All tethers in circulation always match our reserves.”
A web page does give dollar values for assets and liabilities but does not identify the auditors or provide copies of the audit reports, so the claim of being “fully transparent” is somewhat exaggerated. The transparency is as great as that of historical note-issuing banks, however. And perhaps the important test of trustworthiness is that Tethers have in practice been redeemed every day at par for about two years.
Competition as a Market Referendum
Dollar-pegged cryptocurrencies, by contrast to Bitcoin, separate blockchain-secured payments from the speculative holding of an irredeemable private currency. Thus they provide a potential window for learning how much of the demand for cryptocurrencies is transactional, and how much is speculative.
The competition
among dollar-pegged cryptocurrencies provides something of a market referendum on the relative credibility of alternative pegging arrangements. The much larger size achieved by Tether suggests (though not definitively, because other factors are also in play) a popular verdict that its pegging mechanism is more credible than those of CoinoUSD, Nubits, or BitUSD. It will be interesting to watch Tether’s progress from this point on and to observe whether its model is copied by other entrants.
Reprinted from the Cato Institute.
Lawrence H. White is Professor of Economics at George Mason University and
The Freeman contributor. He previously taught at New York University, the University of Georgia, and the University of Missouri – St. Louis. He is a member of the FEE
Faculty Network.
This article was originally published on FEE.org. Read the original article.

 The Market's Glorious Resurrection of Mystery Science Theater 3000
The Market's Glorious Resurrection of Mystery Science Theater 3000




















