As might be expected of early adopters in an anonymous Internet cryptocurrency, many of my customers are information security professionals. It seems that many of them set up so many security measures that they locked themselves out of their Bitcoin. On the other hand, I’ve also heard from many more people who lost their Bitcoin or had it stolen because they either did not follow basic security practices or followed them without understanding their implications and also lost their coins. The inherent balance in information security is that you need walls in place to protect against threats, but the walls you put up to protect yourself can lock you out if you forget your way in.
I, therefore, want to suggest a list of steps that you can take right now to secure your crypto stash. These measures should be both comprehensive enough to keep you safe without being so complicated that you will be locked out of it, or tempted to disable security altogether.
1: Store your wallet seed somewhere safe.
People come to me when they lose their Bitcoins any number of ways, but the one common element in their stories is that they failed to save their recovery seed. Most modern wallets ask you to save your recovery seed/mnemonic phrase somewhere safe when you set up your wallet. You can keep it in a safe place (such as an actual safe) or an encrypted flash drive (I use Veracrypt). Triple-check both the words and the word order, as one person I worked with wrote down his seed incorrectly and lost all of his coins.

A hardware wallet (an electronic device dedicated to storing Bitcoin) such as a Trezor or Ledger is the safest place for your Bitcoin. Read my Trezor review on Amazon to understand the pros and cons of using one.
If you don’t use a hardware wallet, use a wallet which supports strong encryption. The JAXX wallet, for example, can be easily hacked and your coins stolen. I use the Electrum wallet, which allows me to encrypt my wallet file.

Encrypting your whole hard drive is essential if you don’t want anyone with physical or virtual access to your computer to be able to extract all of your data. Modern versions of Windows and Apple iOS make this easy.
If you have a Mac, encrypt your hard drive with FileVault. If you have Windows, you can use BitLocker to do the same thing. Personally, I do not use Windows to make any Bitcoin transactions because securing the operating system is too cumbersome, specifically because of the steps below.
4: Set a firmware password.
Apple computers allow you to set a firmware password which prevents your computer from being accessed without your password or using an external device. This is an additional security measure which makes your computer a lot less useful to thieves as it requires a visit to an Apple store and a proof of purchase to reset it. While older Apple computers had some simple workarounds to disable the firmware lock, modern ones are much more difficult for criminals to unlock.

Hard drive encryption will not help you if someone installs a keylogger when you’re away from your keyboard. Set your computer to auto-lock after a few minutes AFK. Mine is set to auto-lock after five minutes
Here are instructions for Windows and Mac. I also have a “panic button” via a Touch Bar customization which locks my screen on command. I use it whenever I walk away to get coffee, go to the bathroom, etc.
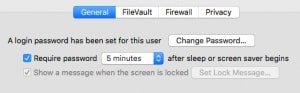
Locking does no good if your computer logs in as you when you turn it on. Make sure auto login is disabled.
7: Use a password manager.
I use the password manager LastPass to store the over 600 passwords of every service I use. I generate a new, strong password for each service I use it with it.
LastPass will offer to suck in and audit all your passwords. My score is not great because, like everyone else, before LastPass, I used the same password for most sites before I started using a password manager. LastPass passwords are encrypted using a master password, which for me is a quasi-random list of words which I don’t use for any other purpose.
However, even if someone gained access to my LastPass credentials, they would not access any of my important services because I also use the following step.
I use LastPass Authenticator in combination with other passwords to access all my important accounts. The LastPass Authenticator iPhone app works with the LastPass Chrome extension to auto-enter credentials for many sites. Multi-factor authentication apps work by cycling a code every 30 seconds which must be entered in addition to the password to access a service. For some services, I also have a physical security token (my Trezor wallet does this, but most people use a YubiKey) which must be physically plugged into my computer to access a site.
Mac OS had a nasty root access bug a few weeks ago. Keep your OS up to date to protect against the latest threats.
10: Use private, offline mode for sensitive operations.
I occasionally need to create a paper wallet or perform other sensitive operations in my web browser. This has two risks:
- The web page may have malicious code which leaks my keys.
- One of my browser extensions may have malicious code (this happened to me a few month ago).
Furthermore, I perform any paper wallet operations with ethernet/Wifi disabled. This prevents malicious code in the wallet from secretly sending your Bitcoin keys to a third party. I then completely quit my web browser before going back online. I also download any browser-based crypto software directly from GitHub rather than random websites.
11: Setup automatic backups.
I’ve set up my MacBook for triple-redundant encrypted hourly backups with Apple Time Machine. This is not nearly as easy with Windows. CrashPlan (available on Windows and Mac) allows encrypted backup to local storage devices. Windows has a built-in backup app, but it’s not nearly as simple or powerful as Time Machine.
While this is not strictly security advice, automating your backups is important from a security perspective. I’ve noticed that people who are not 100% confident in their backups tend to back up important files over flash drives, work computers, email, DropBox, and other services where it is at risk of theft. Some of my clients thought they’d backed up their wallet, but couldn’t figure out which of the 10 flash drives they had actually held their Bitcoins years later. A complete system backup will allow you to restore both the wallet file and the software you used to open it.

Reprinted from Vellum Capital
David L Veksler
David Veksler is the Director of Marketing at FEE.This article was originally published on FEE.org. Read the original article.

No comments:
Post a Comment